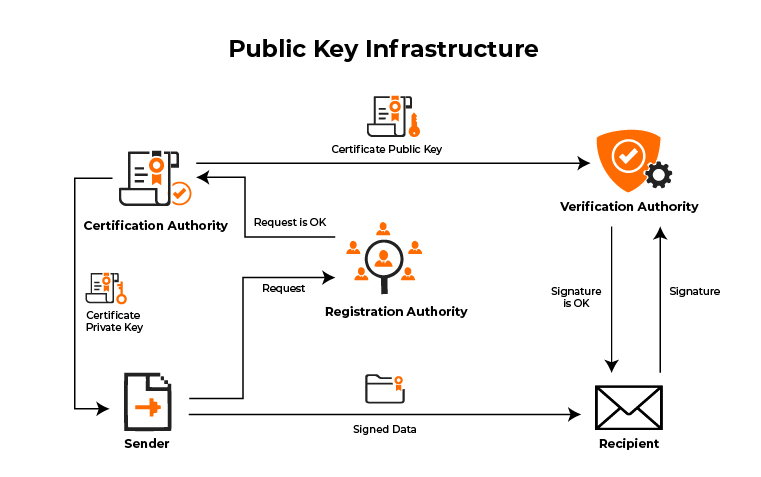
As we already know that PKI is a set of roles, policies, and procedures needed to create, manage, distribute, use and store and revoke the certificates. It is a digital certificate to manage the digital key for security purposes. Most people have a shallow conception of Public Key Infrastructure, PKI is not just a software. It comes down to the point where you also need to understand the pain of the PKI system.
With the better kind of availability PKI system, people have been able to have served most of the customers. The customers could range from the public sector to the private sector. Here, I will bring some of the important points that you must always keep in mind while handling PKI.
Facts that You Should Keep in Mind
- The core of the security is the certificate authority, the certificate authority is a system in the PKI system which helps to issue any certificate of authority in digital format.
- PKI and CA are closely related without the existence of one the other can not exist. The PKI system deserves to get all kinds of certificates for security purposes.
- The PKI system can never exist individually, and the CA should function to get a self-signed certificate. It could be issued to another subordinate person who is also a CA.
- The core of the PKI system is the CA, some of the PKI owners can survive just with the CA component in it. All of it takes place very smoothly under a very controlled environment.
What is HSM?
The HSM can be used virtually and in the cloud environment. The system supports a variety of other systems such as the managing system and many more such things. It also helps in securing the discretion of the private key, protection of the private key, and it also helps to secure the encryption of the management key.
How is HSM applied?
Before we talk further about HSM, we must first find out the application of the HSM so that we are able to figure out how the entire process of PKI is related to HSM.
- It has a Public Key Infrastructure security
- It also allows giving electronic invoice
- Provides digital infrastructure Security
- It helps to secure applications and also helps to manufacture next-generation keys.
- Helps to protect all transactions and all identities, and also some data new technologies
What are the benefits of HSM?
Everything has some benefits and some drawbacks, but if you are thinking of using it then you must first look for the benefits then you will be able to take the fair decision. I know often we have the dilemma in mind about right and wrong, good and bad but this is how you can get over it. You must know the benefits in order to decide if the drawbacks are bad enough or not.
- The operating cost is very low
- The performance of the HSM is very high
- HSM helps you to increase the security
- It is highly resistant to any kind of hacking method
- It helps to support a wide variety of operating system and also various PKI infrastructure
- World-class infrastructure is used in this.
- It stores the private key very securely
- It helps to manage the IP address very securely
Conclusion
We may conclude by saying that we can understand that there are many advantages of the PKI but even if something else is left then you can read some more about it. It would be a nice way to conclude saying that we know the pros and the cons and now we can take the correct decision over it.