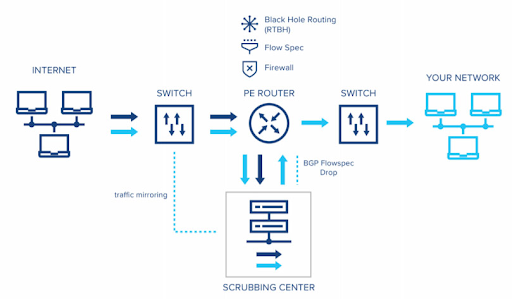
The enemies are everywhere, even in cyberspace. They want to hack your website and steal the data. But sometimes, your competitors want to block your resource to attract your customers. Let’s understand how they reach the goal and how to protect it.
Welcome DOS
DOS or DoS isn’t the famous and key operating system for tablet devices. It is the shortening of the Denial of the System. It supposes breaking the open system’s interaction on one of the following levels:
Number Layer Application Description Interaction method
7 Application Data Final application process HTTP, DNS query storms
6 Presentation Data Representation and encryption SSL abusing
5 Session Data Interhost exchange N/A
4 Transport Segments End-to-end reliability SYN Floods
3 Network Packets Logic of addressing and path determination UDP
2 Datalinks Frames Physical addresses N/A
1 Physical Bits Storage and transmission N/A
Most DOS attacks segregate levels 3, 4, 6, and 7. The remaining levels need different solutions to attack. Problems with any of these levels affect others by hierarchy. Nowadays, the results guarantee the distributed denial of the system (DDoS) attacks, making their source and target identification difficult. Each hacker group blocks the selected layer. So the domestic and offshore DDoS protection should be complex.
Types of attacks
- Infrastructure attacks strive towards layers 3 and 4. They aim to destroy or take control of the content distribution networks. One of the popular broadcasting services suffered these attacks in July. The hackers used infrastructure attacks to broadcast enemy propaganda. That happened because they captured the transport stream and rerouted its stream. Thanking the clear signatures administrators switched off that server and returned the secure broadcast.
- Application attacks tend to block levels six and seven. They tend to change the execution of the program. They’re harder to identify, but modern systems neutralize them efficiently.
How to protect from the threat
- Increase the bandwidth. Choosing between limited and unmetered, prefer the second option. That idea is expensive, but it’s a popular DDoS protection weapon. The enemies will understand that it’s impossible to switch the resource off. However, the multi-storeyed defending system will be helpful too.
- MultiCDN. The content distribution networks always keep their SSL certificates in up-to-date mode. This technology supposes one primary socket and several reserves. Its operator backups up the data in various locations, so the hackers need significant efforts to calculate the original server. CDN balances out the site traffic. The site works as usual.
- Buy the anonymous VPS. That’s not only the bridge between shared and dedicated servers, but it helps to accept cryptocurrencies. It helps to raise the business. Just try.
- Raise the technical specialists. They will plan the counteractions in response to attacks. The software is a good idea, but it’s just code without humans. Take care of the mindful colleagues who keep your business secure.
- Install the DDoS protection server level. There are no small businesses for these attacks, so the protected server is a must-have for the responsible owner. Some operators provide it free service; others want money for that. Study the operator’s agenda to learn about that.
Final word
The rescue of business and content is its owner’s privilege. Nobody will do it for them. The same is true for DDoS control.